This post covers VCP6-DCV Objective 1.2 – Secure ESXi, vCenter Server, and vSphere Virtual Machines. A very interesting chapter indeed, where we cover all the “locks” which an admin can put in place to secure his/here environment. And you don't have to be Linux expert as all this is done without much difficulty!
For whole exam coverage I created a dedicated VCP6-DCV page. Or if you're not preparing to pass a VCP6-DCV, you might just want to look on some how-to, news, videos about vSphere 6 – check out my vSphere 6 page. If you find out that I missed something, don't hesitate to comment.
Knowledge
- Enable/Configure/Disable services in the ESXi firewall
- Enable Lockdown Mode
- Configure network security policies
- Add an ESXi Host to a directory service
- Apply permissions to ESXi Hosts using Host Profiles
- Configure virtual machine security policies
- Create/Manage vCenter Server Security Certificates
—————————————————————————————————–
Enable/Configure/Disable services in the ESXi firewall
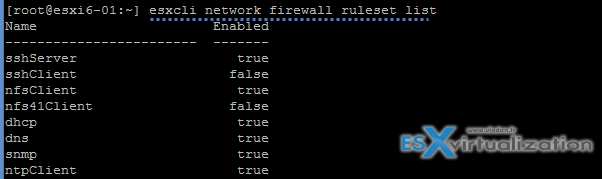
How to enable/disable services in the ESXi firewall – The hard way (via CLI)
Check whih services are active
esxcli network firewall ruleset list
Open firewall port via CLI:
esxcli network firewall ruleset set -e true -r httpsClient
![]()
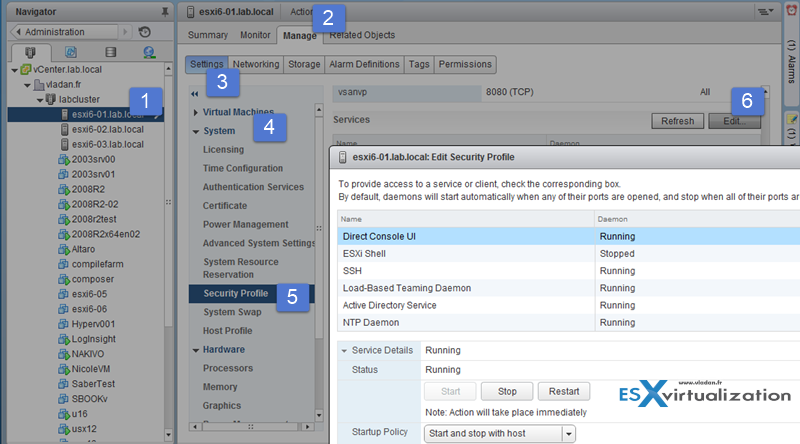
How to enable/disable services in the ESXi firewall – The easy way (via vSphere client)
Note that you can do the same by selecting the host through vSphere client > configuration > security profile > Firewall
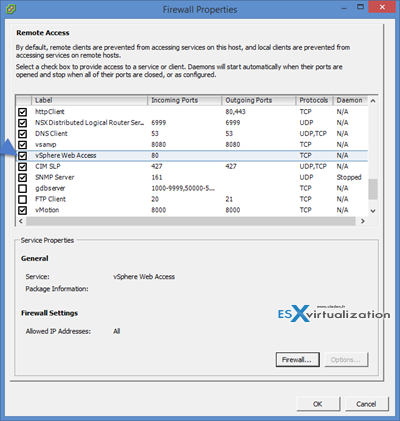
Services can be Started, Stopped, or Restarted. Services can be configured to Start and stop with host, Start and stop manually, or Start and stop with port usage.
ESXi Shell and SSH are disabled (Set to Start and stop manually) by default. ESXi Shell and SSH can be enabled/disabled in the DCUI from the Troubleshooting Mode Options menu.
Enable Lockdown Mode
When you enable lockdown mode, you can't connect directly from the console. the host is accessible only through the vSphere client directly or via vCenter server.
Lockdown Modes:
- Disabled – Lockdown mode is disabled.
- Normal – Lockdown mode is enabled. The host can only be accessed from vCenter or from the console (DCUI).
- Strict – Lockdown mode is enabled. The DCUI service is stopped. The host can not be accessed from the console (DCUI).
[TIP]: You can activate DCUI from within SSH session
Type this after login in with Putty or other SSH client.
dcui
There you see the DCUI screen
vSphere 6 introduced “Exception users” which are users with local accounts or Microsoft Active Directory accounts with permissions defined locally on the host where these users have host access. You can define those exception locally on the host, but it’s not recommended for normal user accounts, but rather for service accounts. You should set permissions on these accounts to strict minimum and only what’s required for the application to do its task and with an account that needs only read-only permissions to the ESXi host.
This is basically the same principle of local server accounts on Windows member server, where you can create local accounts, but as a best practice to give them only the permissions they need…
Smart Card Authentication to DCUI – There is new function, but apparently it is for U.S. federal customers only. It allows DCUI login access using a Common Access Card (CAC) and Personal Identity Verification (PIV). In this case the ESXi host must be part of Microsoft AD.
Configure network security policies
Network security policies are defined on two places:
- vSwitch level
- Portgroup level
Three different policies:
- Promiscuous mode – If set to Accept then it allows the guest OS to receive all traffic observed on the connected vSwitch or PortGroup (the switch becames a HUB basically – with all the inconveniences, packet colisions, performance degradation etc… ). By default it's Reject
- MAC address changes – A host is able to accepts requests to change the effective MAC address to a different address than the initial MAC address. By default it's Accept
- Forged transmits – A host does not compare source and effective MAC addresses transmitted from a virtual machine. By default it's Accept
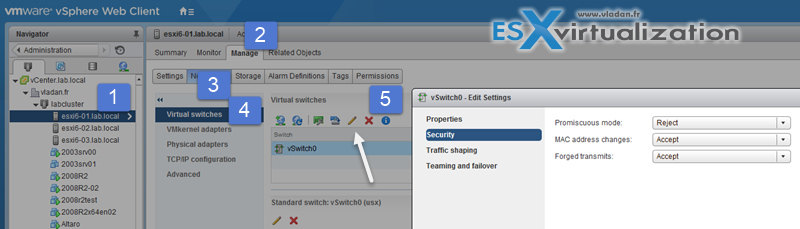
Or via vSphere client (more convenient)
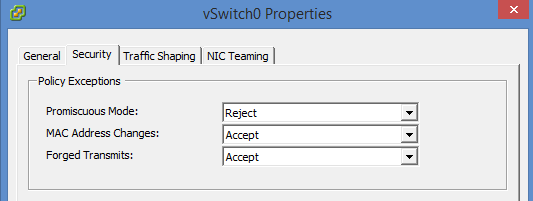
MAC address changes and Forged transmits if set to Reject, than it protects against MAC address spoofing.
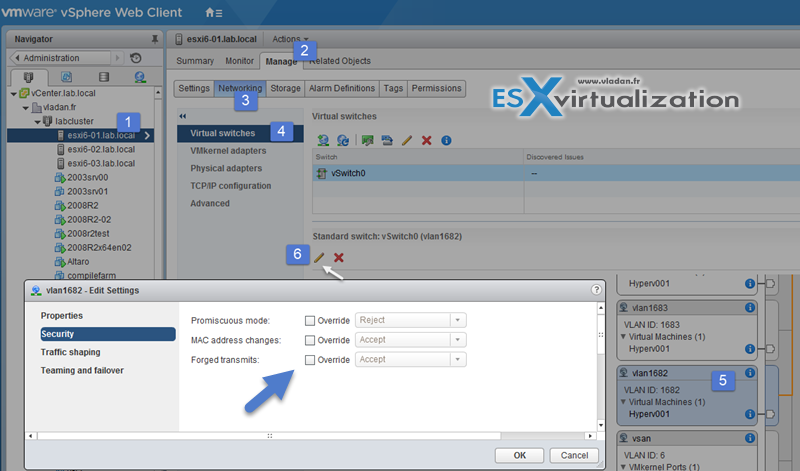
If changing the settings at the Portgroup level there is an Override checkbox allowing you to set the policy on a portgroup rather than on the vSwitch.
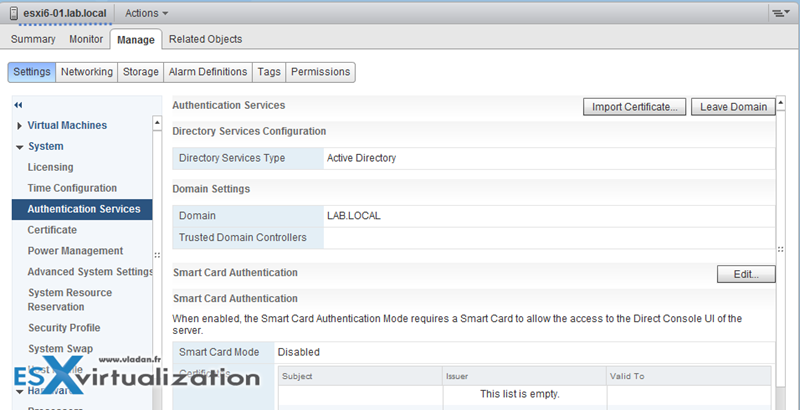
Add an ESXi Host to a directory service
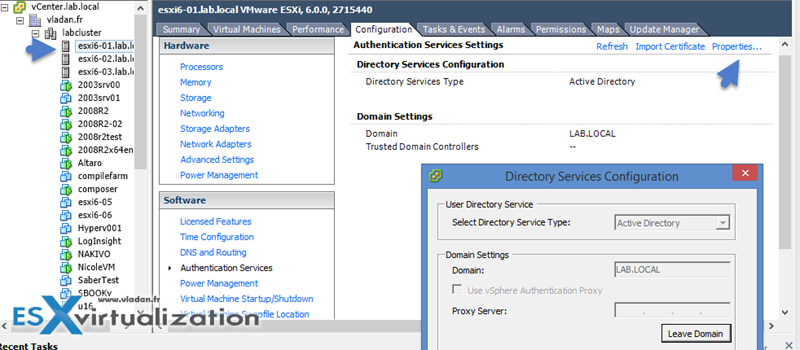
A special AD group named “ESX Admins” shall be manually created before host is joined to AD. Why? Because like this All members of this group (ESX admins) are automatically assigned with the Administrator role on the host when this host is joined to AD. If not the permissions has to be applied manually.
vSphere web client > Hosts and clusters > Select ESXi host > Manage > Settings > Authentication services.
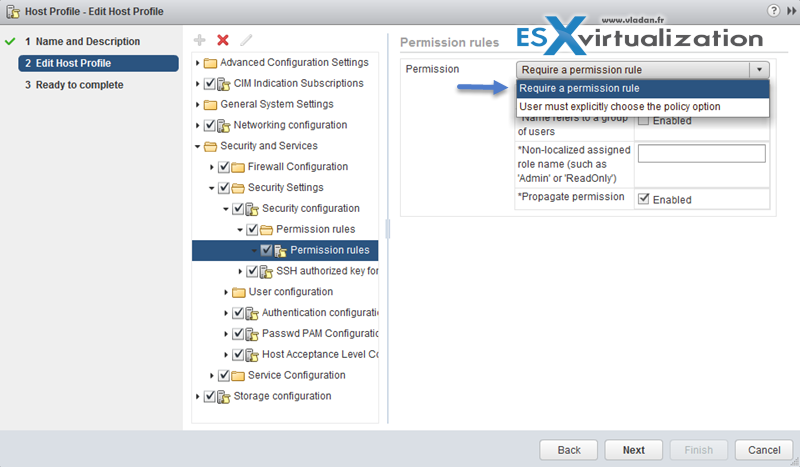
Apply permissions to ESXi Hosts using Host Profiles
Host profiles are very cool feature allowing to homogenize configuration across ESXi hosts and automate compliance. In some cases, host profiles can be also useful when for example you need to reset esxi root password on a host.
Check vSphere Security guide (PDF) on p. 133, but basically this procedure apply:
- Select the host profile > Click Actions > Edit Host Profile (or right click > edit settings)
- Expand Security and Services
- Select the Permission Rules folder > click the Plus Sign
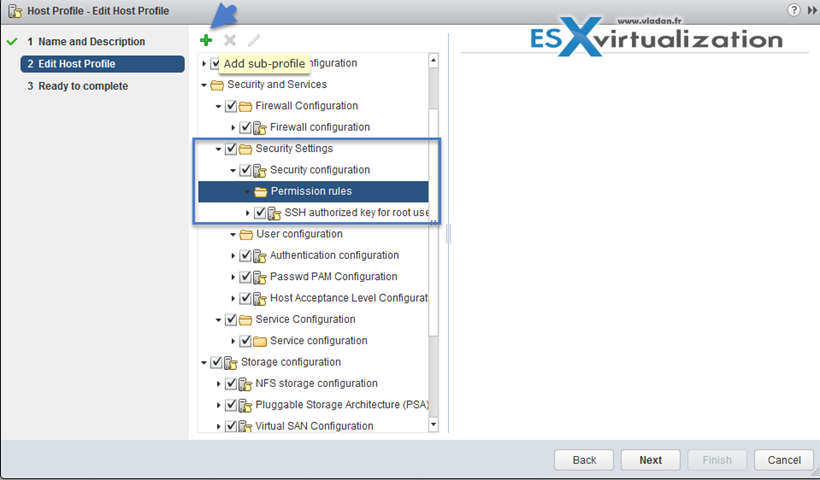
Root password is encrypted within the host profile, however by joining hosts to AD via Host profiles leaves password in plain text… -:(.
Configure virtual machine security policies
VMs are fragile. The same for Guest OS. Treat them accordingly … -:). Seriously, you should patch to the latest release for the OS patches, Antivirus patches and/or Malware patches…. That's a bare minimum to prevent system corruption.
- Be organized – Use templates to deploy virtual machines
- Minimize use of virtual machine console
- Prevent virtual machines from taking over resources
- Disable unnecessary functions inside virtual machines – usually Windows/Linux services can be stopped, to put them on manual instead of automatic startup, etc..
- Remove unnecessary hardware devices – floppy, printers, sound devices… All you don't need you can remove to have lower overhead.
- Disable unused display features
- Disable unexposed features
- Disable HGFS file transfers
- Disable copy and past operations between guest operating system and remote console (by default is disabled – on per host level, but you can add an advanced settings:)
isolation.tools.copy.disable = true
isolation.tools.paste.disable = true
- Limiting exposure of sensitive data copied to the Clipboard
- Restrict users from running commands within a virtual machine
1. Click Administration and select Roles > click create role > NO Guest Access > select all privileges
2. Deselect All Privileges >Virtual machine > Guest Operations to remove the Guest Operations set of privileges > validate OK.
- Prevent a virtual machine user or process from disconnecting devices
- Modify guest operating system variable memory limit
- Prevent guest operating system process from sending configuration messages to the host
- Avoid using Independent Nonpersistent Disks – keep in mind non persistent disks are not affected by snapshots. If you use snapshots. A redo log is created to capture all subsequent writes to that disk. However, if the snapshot is deleted, or the virtual machine is powered off, the changes captured in that redo log are discarded for that Independent Non-persistent VMDK.
Create/Manage vCenter Server Security Certificates
Certificates got easier with vSphere 6 as those can be viewed and renewed within vSphere Web client.
There are two operations modes:
- Root CA – (by default)
- Issuer CA – possibility integrate Microsoft Certification authority. In this case you’ll create the CSR (request) > Go to Microsoft Cert Server and get certificate.
To view certificates:
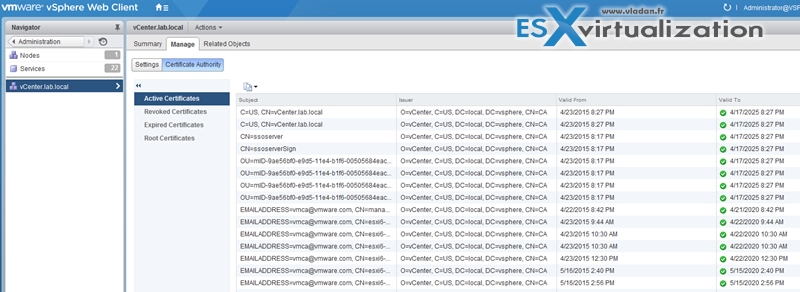
The VMware Certificate Authority (VMCA) provisions vCenter Server components and ESXi hosts with certificates that use VMCA as the root certificate authority by default.
The vSphere Certificate Manager utility allows you to perform most certificate management tasks interactively from the command line.
Example. On Windows you must go to this directory:
C:\Program Files\VMware\vCenter Server\vmcad\certificate-manager.bat
Link to Online documentation for using vSphere Certificate manager utility.
vSphere Certificate Manager prompts you for the task to perform, for certificate locations and other information as needed, and then stops and starts services and replaces certificates for you.
vCenter Certificate Utilities:
- vSphere Certificate Manager utility – certificate replacement tasks from a command line utility.
- Certificate management CLIs – dir-cli, certool, and vecs-cli command line utilities.
- certool can Generate and manage certificates and keys. Part of VMCA.
- dir-cli is a able to create and update certificates in VMware Directory Service. Part of VMAFD.
- ves-cli can manage the contents of VMware Certificate Store instances. Part of VMAFD
- vSphere Web Client certificate management – view certificate information in the Web Client
Tools
- vSphere Installation and Setup Guide
- vSphere Security Guide
- What’s New in the VMware vSphere® 6.0 Platform
- Security of the VMware vSphere® Hypervisor
- vSphere Administration with the vSphere Client Guide
- VMware Hardened Virtual Appliance Operations Guide added to Tech Resource Directory
- vSphere Client / vSphere Web Client