Securing remote workers is not easy in any environment. Whether it is in the small business company or large enterprise environment. In fact, it is quite a complex task because IT administrators has to work with compromises. On one side they’re asked to provide remote access to the company’s IT infrastructure and at the same time, they must protect those data from threads.
A proper isolation on certain levels must be done. For example, they can do an OS-based isolation where only thin client endpoints are used for connections to the Desktop as a service (DaaS) service provider. In this case, the company has to buy a thin client, keyboard and monitor, for each employee working from home.
From a security standpoint this is one of the best solutions as there is no data stored on thin clients and usually those devices run only a small Linux distribution out of a Firmware SD card to show up the remote connection icon on the desktop. The user then clicks the RDP icon connection and connects to the remote DaaS provider’s desktop.
However, this kind of solution is usually more costly compared to Bring Your Own Device (BYOD) policy. There is a real risk that a remote worker will access the corporate network from an already-compromised personally owned laptop or workstation. In this scenario the malware can have direct access to the enterprise’s file systems and encrypt or cripple thousands of files. A very high security risk indeed.
With a little of compromise, we’ll see that it is still possible to secure the connection from personal computers or laptops to the DaaS.
With DaaS, there’s no data stored on a local machine so we don’t have to worry about some data loss on the user’s laptops. At the end of the day, it’s their own responsibility to take care of their own data.
DaaS providers security measures and compliance are usually making sure that your cloud stored data is safe and secure, with a restore possibility.
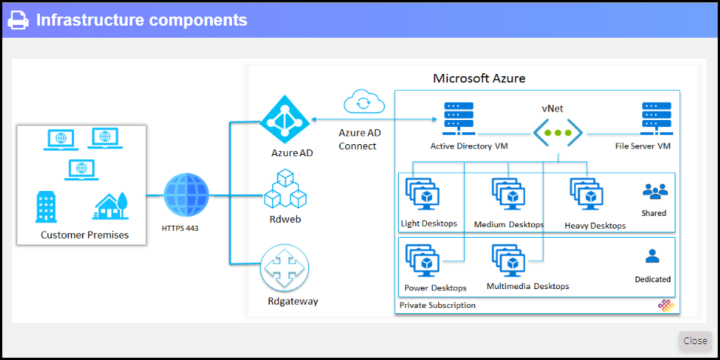
Four areas that shall be restricted for better DaaS security
Why we’re cautious with users and their own devices? It’s because those devices, usually called as a “Bring your own device” (or BYOD), are personal devices not managed by corporate security standards.
They might not have the best antivirus/antimalware protection. They might not use firewall and be already compromised and infected by a malware.
In case it is a Windows computer, it might not have the latest Microsoft security patches installed. It might be a Windows computer or laptop that runs older OS such as Windows 7 or even older. Those systems are on the list of outdated OS listed by Microsoft so there are no longer the mandatory security patches available.
Sometimes malware simply sneaks in and stay in a stand-by mode during weeks/months. Only after it activates and starts doing some damage to the local file system.
IT administrators can configure some security settings for remote connections to the DaaS provider datacenter. This is usually done at the domain policy level via Group Policy Management Console (GPMC).
Those areas are:
- Clipboard redirection – this is usually used for copy/paste or cut/paste operations. This function is used both ways. From remote to local or from local to remote. It basically allows full file copy or download.
- Drive mapping/redirection – corporate systems default settings might be set to create a drive mapping which allows the remote user to access their local drive(s) through the remote PC (thus allowing file copy/download). This is certainly a bad idea from the security standpoint.
- COM port redirection – this feature is used to make some local COM devices available to the remote PC. Again, security concerns.
- LPT port redirection – this might be little bit problematic as users might need to print paper documents. However, this one is also a security issue. LPT port redirection can be used to make some local Line Printer Terminal devices available to the remote PC. So this way, allowing basically some local printing of remote files.
The settings are available as a GPO and in order to prevent the users from using each feature, you need to enable the group policy that actively blocks it, thus overriding the default value that allows it for all users.
Other security tips to ensure secure access for DaaS
Updated RDP software – admins shall keep up-to-date the RDP connection software on their client’s computers. In fact, they should only run the latest versions of both the client and server software by enabling and auditing automatic Microsoft Updates. If you are using Remote Desktop clients on other platforms, you should make sure they are still supported and that you have the latest versions. Older versions of such a software might be outdated or not supporting the latest high encryption.
Firewall restrictions – admins shall use firewall rules where they can restrict access to RDP listening ports. They can also use RDP gateway where they can change the default RDP port. Why is that? It’s because hackers usually scan remote systems and checks whether those ports are open.
Two-factor authentication – 2FA is becoming widely available at a reasonable cost. IT admins should consider using 2FA for remote users because this helps to protect their connections against hackers. Another way to secure access is also by using smartcards.
Use strong passwords – this might not be very popular, but it is a very effective way of protecting remote desktop connections. Hackers usually use brute force software to guess user’s passwords but by using complex passwords, admins make their exploits more difficult.
Set account lockout policy – this goes with the conjunction of the point above. Basically, it sets how many times you can try to enter with an incorrect password. By setting your DaaS systems to lock an account for a set number of incorrect guesses, you will help prevent hackers from using automated password guessing tools from gaining access to your system.
Final Words
IT admins have a difficult task today. They must enable remote workers with remote access to the cloud computing environment and cloud desktops while ensuring secure access. The remote workers are relying heavily on web conferencing and collaboration tools to do their jobs.
Those tools also can get compromised. For example, we could recently hear about “Zoom-bombing” being the most prominent, but not the only one.
Security will be a very important part of future remote working. With the pandemic, we’re facing now and the new normal of working from anywhere, the security of remote connections is an important factor.
More posts from ESX Virtualization:
- vSphere 7 U2 Released
- vSphere 7.0 Download Now Available
- vSphere 7.0 Page [All details about vSphere and related products here]
- VMware vSphere 7.0 Announced – vCenter Server Details
- VMware vSphere 7.0 DRS Improvements – What's New
- How to Patch vCenter Server Appliance (VCSA) – [Guide]
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)