You might need to create Custom ESXi 5.x firewall rule for different reasons. One of them might be a custom made in-house software application. Services like FTP, SFTP, Telnet or SSH are not enabled by default, and the ports for these services are closed. In the list of services, there is not a possibility for an administrator to add a custom firewall rule through the GUI. The process is possible through the CLI. So how to create custom ESXi 5.x Firewall rule?
ESXi 5.x firewall is not based on iptables as it was the case in pre-esxi5.x release. The ESXi firewall retain its configuration during the migration process, and it's active by default for new clean installations of ESXi 5.x.
You maight need to open the firewall for the defined port on TCP or UDP that is not defined by default in Firewall Properties under Configuration > Security Profile on the vSphere Client. Custom firewall rules is also on the VCP and both VCAPs blueprints so if you're studying to pass one of those VMware certification exams, you'll need this knowledge.
ESXi 5.x uses rule list for firewall rules. The rule list is written in config file, which is an XML file located here:
/etc/vmware/firewall/service.xml
The SSH access must be enabled so you can Putty to your ESXi host. The namespace esxcli network firewall gives you the options needed.
How to create custom ESXi 5.x Firewall rule?
It's not really difficult to create a custom rule, but you need to know the outline, follow the pattern and also you'll need to know how to work with VI editor… (Note that you can also do part of the job via WinSCP).
Step 1: Backup first the original service.xml file by running this command, but first step in to the directory by
cd /etc/vmware/firewall
And then
cp service.xml service.xml.original
Step 2: Change permissions of the service.xml file so we can do modifications
chmod 644 service.xml
and
chmod +t service.xml
Step 3: Open the service.xml file in VI editor
vi service.xml
Now the most difficult part as there are very strict rules on what a ruleset has to contain.
- A numeric identifier for the service, if the configuration file contains more than one service.
- A unique identifier for the rule set, usually the name of the service.
- For each rule, the file contains one or more port rules, each with a definition for direction, protocol, port type, and port number or range of port numbers.
- A flag indicating whether the service is enabled or disabled when the rule set is applied.
- An indication of whether the rule set is required and cannot be disabled.
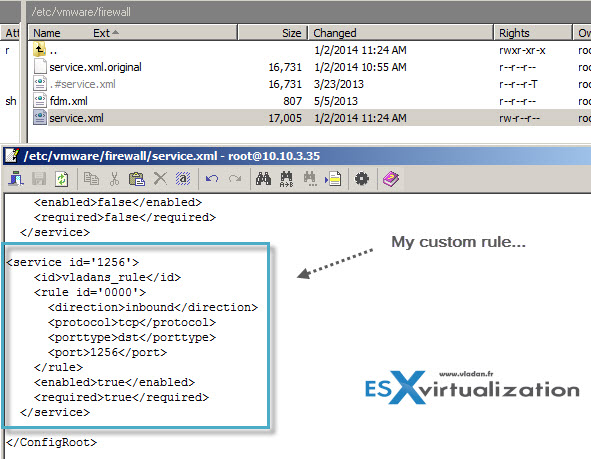
Example: Rule Set Configuration File
<service id='1256′>
<id>vladans_rule</id>
<rule id='0000′>
<direction>inbound</direction>
<protocol>tcp</protocol>
<porttype>dst</porttype>
<port>1256</port>
</rule>
<enabled>true</enabled>
<required>true</required>
</service>
The best way is to copy one of those rules and adapt it to your needs (changing the ID number, ID, rule ID etc…. ) Note that the dst in the example means destination.
On the example below is screenshot from WinSCP utility, if you prefer …
Step 4 – Re-change the permissions and refresh the firewall…
chmod 444 service.xml
and
esxcli network firewall refresh
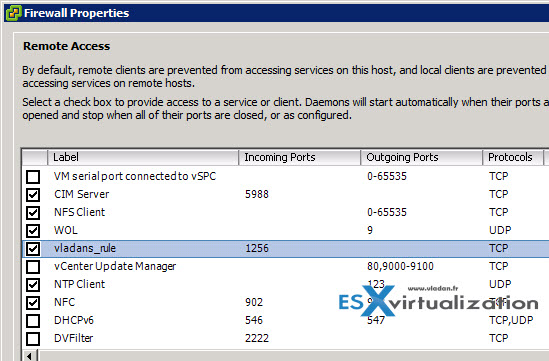
Step 5: List the rules by
esxcli network firewall ruleset list
and (or) control that the rule apears through the vSphere client.
Thats all. If not there are individual commands which can be passed to open ports, but not quite sure those changes persists through reboots. By using this method the config persists through reboots.
update: just checked with 5.5 u1, and it does not persist across reboot. It was persistant (and tested) with the 5.1 version.
You can use this kb when you want to make it persistant across reboots:
- User defined xml firewall configurations are not persistent across ESXi host reboots (2007381)
Sources:
- VMware KB 2008226 – Creating custom firewall rules in VMware ESXi 5.0
- VMware KB 2005304 – Adding a third-party firewall extension to ESXi 5.0
- VMware Online Documentation

Do you know if they give you winscp or something similar on the VCAP-DCA exam?
Yes, they give winscp.
this is not persistent
it either has to be the loaded in to a vib and then installed
or you need an ugly hack to rc.local
Changing the port used by SSH on an ESXi 5.0 host (2011818)
No, custom firewall rules are not preserved through reboots using this method unless you…
To fix this make it into a .tgz and add it to bootbank and boot.cfg
Make the new rule test.xml
mkdir -p /tmp/etc/vmware/firewall
move test.xml in
from /tmp
tar czvf test.tgz etc
cp test.tgz /bootbank
edit boot.cfg and add “— test.tgz” to end of modules
run auto-backup to make persistent
Thanks for your comment and letting me know. This is an old post, created for v 5.0. The behaviour changed in 5.5. The post has been updated (link to a VMware kb).