We continue our daily work on VMware Certified Professional – VMware vSphere Foundation Administrator (2V0-16.25) study guide series! The upcoming VCP-VVF Study Guide which shall be released as a PDF when completed – https://www.vladan.fr/vcp-vvf-administrator/.
Today, we’re starting Objective 4.2 – VVF: Manage, focusing on Given a scenario, configure Identity Management and Role-based Access Control (RBAC) in VMware vSphere Foundation. Identity Management and RBAC in VMware vSphere Foundation (VVF) 9.0 ensure secure access to vCenter Server and ESXi hosts by integrating identity sources and assigning roles to control permissions.
This objective is critical for the 2V0-16.25 exam, testing your ability to configure secure access in real-world scenarios. Building on our previous posts (e.g., Objective 4.1 on VVF deployment and Supervisor configuration), we’ll provide detailed steps, practical tips, and exam-focused guidance using a realistic scenario, aligned with VMware’s official vSphere 9.0 documentation https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere/9-0.html. Let’s get technical and configure Identity Management and RBAC!
Why Identity Management and RBAC Matter
Identity Management in VVF 9.0 integrates external identity sources (e.g., Active Directory, LDAP) with vCenter’s Single Sign-On (SSO) to authenticate users, while Role-based Access Control (RBAC) defines permissions through roles assigned to users or groups. These features ensure secure, granular access to vCenter, ESXi hosts, and resources like VMs and clusters. Objective 4.2, Part 1, evaluates your ability to configure identity sources and RBAC in scenarios requiring secure administration and delegated access. We’ll cover the process of setting up Active Directory (AD) integration and assigning roles, ensuring you’re prepared for the exam and real-world administration.
Scenario: Configuring Identity Management and RBAC in VVF
Let’s use a typical exam scenario: A medium-sized business has deployed a VVF 9.0 environment with a 4-host cluster (“VVF-Cluster”) running 20 VMs (10 web servers, 5 databases, 5 VDI desktops) on a vSAN datastore (“vSAN-Datastore”), managed by vCenter 9.0 (IP: 192.168.1.20, hosts at 192.168.1.10-13). The environment includes vSphere HA, DRS, a vSphere Distributed Switch (“vDS-VVF”), and a Supervisor for Kubernetes workloads (Objective 4.1, Part 3). The business wants to secure access by integrating with an Active Directory domain (lab.local, DC at 192.168.1.50) and assigning roles to three teams: Admins (full control), DevOps (manage Kubernetes namespaces and VMs), and Operators (monitor and restart VMs). You must: configure Identity Management with AD integration and set up RBAC to assign appropriate roles to these teams. This scenario tests your ability to configure Identity Management and RBAC for the 2V0-16.25 exam.
Configuring Identity Management and RBAC: Step-by-Step
Configuring Identity Management and RBAC involves integrating an identity source (Active Directory) with vCenter SSO and assigning roles to control access. Below is a detailed guide with manual steps for the scenario, using the vSphere Client for VVF 9.0.
1. Configure Active Directory Integration
Purpose: Integrate vCenter with Active Directory to authenticate users via SSO, enabling centralized user management.
Detailed Process:
Verify Prerequisites:
Ensure the AD domain controller (192.168.1.50, lab.local) is accessible from vCenter (192.168.1.20).
Confirm DNS is configured: vCenter resolves “dc.lab.local” to 192.168.1.50 (Administration → Single Sign-On → Configuration → DNS).
Prepare AD groups: “VVF-Admins”, “VVF-DevOps”, “VVF-Operators” with respective users (e.g., [email protected], [email protected], [email protected]).
Add AD as an Identity Source:
- Log in to vCenter at https://192.168.1.20/ui using SSO credentials ([email protected]).
- Navigate to Menu → Administration → Single Sign-On → Configuration → Identity Provider → Active Directory (Integrated Windows Authentication).
- Select Add Identity Source:Identity Source Type: Active Directory (Windows Integrated Authentication).
- Domain Name: lab.local.
- Use Machine Account: Select for simplicity (leverages vCenter’s AD computer account).
- Base DN for Groups: Set to “DC=lab,DC=local” (or specific OU if restricted).
- Click Add to integrate AD.
Add AD Groups to SSO:
- Navigate to Administration → Single Sign-On → Users and Groups → Groups.
- Add AD groups: “VVF-Admins”, “VVF-DevOps”, “VVF-Operators” (search for “lab.local\VVF-Admins”).
Verification:
- Test login: Log out and log in as [email protected] to confirm AD authentication.
- Check Administration → Single Sign-On → Users and Groups to verify AD groups are listed.
Scenario Example: Integrate vCenter (192.168.1.20) with AD (lab.local, 192.168.1.50) and add “VVF-Admins”, “VVF-DevOps”, “VVF-Operators” groups for authentication.
Study Tip: Practice AD integration in VMware Hands-On Labs https://labs.hol.vmware.com/. Memorize the SSO configuration steps and DNS requirements for the exam.
2. Create Custom Roles for RBAC
Purpose: Define custom roles with specific permissions to meet the access needs of Admins, DevOps, and Operators teams.
Detailed Process:
Create Admin Role:
- Navigate to Menu → Administration → Access Control → Roles → Add Role.
- Name: “VVF-Full-Admin”.
- Description: “Full control for VVF administrators”.
- Permissions: Select all privileges (e.g., Host, Virtual Machine, Datastore, Network, vSAN, Workload Management) for full control.
- Click Create to save.
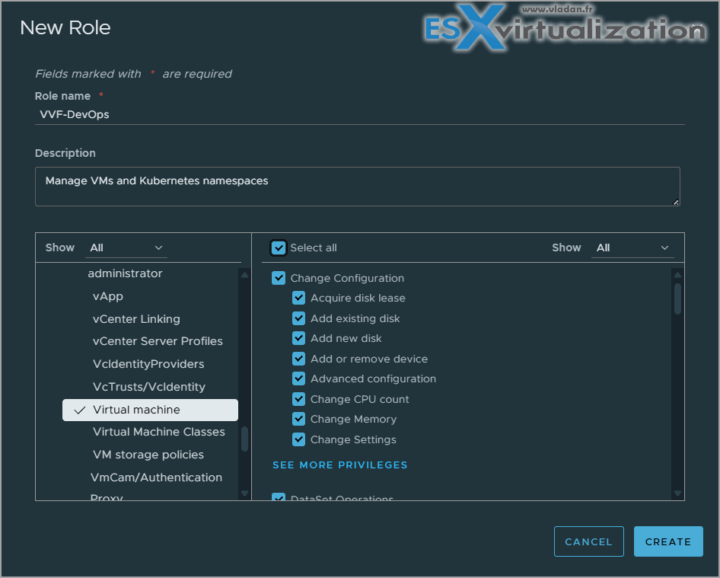
Create DevOps Role:
- Navigate to Menu → Administration → Access Control → Roles → Add Role.
- Name: “VVF-DevOps”.
- Description: “Manage VMs and Kubernetes namespaces”.
- Permissions:Virtual Machine:Inventory: Create, Delete.
- Configuration: All (e.g., Add New Disk, Modify Settings).
- Interaction: Power On, Power Off, Reset, Console.
- Workload Management:Namespace.Manage: Create and configure namespaces.
- Workload.Manage: Deploy and manage pods.
- Datastore: Browse, Allocate Space.
- Network: Assign Network.
- Click Create to save.
Create Operator Role:
- Navigate to Menu → Administration → Access Control → Roles → Add Role.
- Name: “VVF-Operator”.
- Description: “Monitor and restart VMs”.
- Permissions:Virtual Machine: Power on/off, reset, view configuration.
- Host: View metrics and status.
- Datastore: Browse only.
- Click Create to save.
Verification:
- Check Administration → Access Control → Roles to confirm “VVF-Full-Admin”, “VVF-DevOps”, and “VVF-Operator” roles are listed with correct privileges.
Scenario Example: Create “VVF-Full-Admin” (full control), “VVF-DevOps” (VMs and Kubernetes), and “VVF-Operator” (monitor/restart) roles for the three teams.
Study Tip: Memorize key privileges for roles (e.g., VM, Workload Management, Datastore). Practice creating custom roles in a lab for the exam.
3. Assign Roles to AD Groups
Purpose: Assign roles to AD groups to grant permissions at the appropriate vSphere objects (e.g., cluster, namespace, VMs).
Detailed Process:
Assign Admin Role:
- Navigate to Hosts and Clusters → VVF-Cluster → Permissions → Add Permission.
- Select Identity Source: lab.local.
- Search for “VVF-Admins” group and assign the “VVF-Full-Admin” role.
- Enable Propagate to children to apply to all objects in “VVF-Cluster”.
Assign DevOps Role:
- Navigate to Workload Management → Namespaces → Microservices-Namespace → Permissions → Add Permission.
- Select Identity Source: lab.local.
- Search for “VVF-DevOps” group and assign the “VVF-DevOps” role.
- Also assign “VVF-DevOps” role to Hosts and Clusters → VVF-Cluster → VMs and Templates for VM management.
Assign Operator Role:
- Navigate to Hosts and Clusters → VVF-Cluster → VMs and Templates → Permissions → Add Permission.
- Select Identity Source: lab.local.
- Search for “VVF-Operators” group and assign the “VVF-Operator” role.
- Enable Propagate to children for all VMs (web, database, VDI).
Verification:
- Log in as [email protected] (VVF-Admins) to confirm full access (e.g., create VMs, configure vSAN).
- Log in as [email protected] (VVF-DevOps) to verify namespace and VM management (e.g., deploy a pod in “Microservices-Namespace”).
- Log in as [email protected] (VVF-Operators) to confirm monitoring and VM restart capabilities.
- Scenario Example: Assign “VVF-Full-Admin” to “VVF-Admins” on “VVF-Cluster”, “VVF-DevOps” to “VVF-DevOps” on “Microservices-Namespace” and VMs, and “VVF-Operator” to “VVF-Operators” for VMs.
- Study Tip: Practice assigning roles to AD groups in a lab, focusing on permission propagation and object-specific access. Understand role granularity for the exam.
4. Test and Verify Access Control
Purpose: Validate that users have the correct permissions and that RBAC enforces security.
Detailed Process:
Test Admin Access:
- Log in as [email protected] and perform tasks: create a VM, configure vSAN, deploy a namespace.
- Confirm full access to all objects in Hosts and Clusters, Storage, Networking, and Workload Management.
Test DevOps Access:
- Log in as [email protected] and:Deploy a pod in “Microservices-Namespace” (e.g., kubectl -n Microservices-Namespace run nginx-pod –image=nginx).
- Create and power on a VM in “VVF-Cluster”.
- Attempt to modify vSAN settings (should fail, as not included in “VVF-DevOps” role).
Test Operator Access:
- Log in as [email protected] and:View VM status and metrics for web, database, and VDI VMs.
- Restart a VM (e.g., web server).
- Attempt to create a VM or namespace (should fail, as not included in “VVF-Operator” role).
Verification:
- Check Home → Administration → Access Control → Permissions for correct role assignments.
- Review Events in vCenter for login and action attempts to confirm RBAC enforcement.
Scenario Example: Test [email protected] (full control), [email protected] (VMs and namespaces), and [email protected] (monitor/restart) to ensure RBAC works as configured.
Study Tip: Practice testing permissions in a lab, focusing on restricted actions (e.g., Operators cannot create VMs). Understand permission conflicts for the exam.
Exam Scenarios and Tips
Scenarios:
Scenario: An AD user cannot log in to vCenter. What should you check?
Answer: AD integration settings, DNS resolution, and user group membership in SSO.
Scenario: A DevOps user cannot deploy a pod. What’s a likely issue?
Answer: Missing Workload Management permissions in the “VVF-DevOps” role or incorrect namespace assignment.
Scenario: Operators can modify vSAN settings. How can you fix this?
Answer: Adjust the “VVF-Operator” role to exclude vSAN privileges and reassign permissions.
Study Tips:
- Practice AD integration and RBAC configuration in VMware Hands-On Labs https://labs.hol.vmware.com/.
- Memorize: SSO identity sources (AD, LDAP), role creation, permission assignment, and propagation.
- Review VMware vSphere 9.0 documentation https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere/9-0.html for Identity Management and RBAC details.
- Focus on scenario-based questions involving user access and permission troubleshooting.
Resources:
- VCP-VVF Study Guide Page: https://www.vladan.fr/vcp-vvf-administrator/
- VMware vSphere 9.0 Documentation: https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere/9-0.html
Sample Exam Questions
Which component manages Identity Management in VVF 9.0?
A. vSphere HA
B. Single Sign-On (SSO)
C. vSAN Datastore
D. vSphere Distributed Switch
Answer: B. Single Sign-On (SSO).
What is required to integrate Active Directory with vCenter?
A. vSphere DRS
B. DNS resolution
C. Thin Provisioning
D. Content Library
Answer: B. DNS resolution.
How do you restrict a user to monitoring VMs in VVF?
A. Assign the Administrator role
B. Create a role with view and power on/off privileges
C. Enable vSAN encryption
D. Configure a namespace
Answer: B. Create a role with view and power on/off privileges.
Final Words
The post is based on fiction scenario, use with caution. The purpose is to help you to learn and achiever some results. Configuring Identity Management and RBAC in VVF 9.0 is a vital skill for the 2V0-16.25 exam and secure virtualization administration. By integrating Active Directory and assigning tailored roles, you can ensure secure, granular access for different teams. The upcoming VCP-VVF Study Guide Page, available at https://www.vladan.fr/vcp-vvf-administrator/, will be released as a PDF to support your preparation. Stay tuned for the next part of Objective 4.2! Happy studying, and good luck on your VCP-VVF journey!
More posts from ESX Virtualization:
- 5 New VMware Certifications for VVF and VCF
- VMware Alternative – OpenNebula: Powering Edge Clouds and GPU-Based AI Workloads with Firecracker and KVM
- Proxmox 9 (BETA 1) is out – What’s new?
- Another VMware Alternative Called Harvester – How does it compare to VMware?
- VMware vSphere 9 Standard and Enterprise Plus – Not Anymore?
- VMware vSphere Foundation (VVF 9) and VMware Cloud Foundation (VCF 9) Has been Released
- Vulnerability in your VMs – VMware Tools Update
- VMware ESXi FREE is FREE again!
- No more FREE licenses of VMware vSphere for vExperts – What’s your options?
- VMware Workstation 17.6.2 Pro does not require any license anymore (FREE)
- Migration from VMware to another virtualization platform with Veeam Backup and Replication
- Patching ESXi Without Reboot – ESXi Live Patch – Yes, since ESXi 8.0 U3
- Update ESXi Host to the latest ESXi 8.0U3b without vCenter
- Upgrade your VMware VCSA to the latest VCSA 8 U3b – latest security patches and bug fixes
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- vSphere 8.0 Page
- ESXi 7.x to 8.x upgrade scenarios
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster

Leave a Reply