Hornetsecurity who is a provider of cloud-based email security solutions and data protection solutions (formerly Altaro VM Backup) has recently released its annual Cyber Security Report 2024, which analyzes the Microsoft 365 (M365) threat landscape based on real-world data collected from billion of emails processed in 2023. (3.5 billion every month). The report reveals the current state of M365 security, the most critical and emerging cyber security threats, and the predictions and recommendations for 2024. It's a free download here.
In this blog post, we will summarize the key findings and insights from the report, and highlight the main challenges and opportunities for M365 users and admins in the coming year.
The Current State of M365 Security
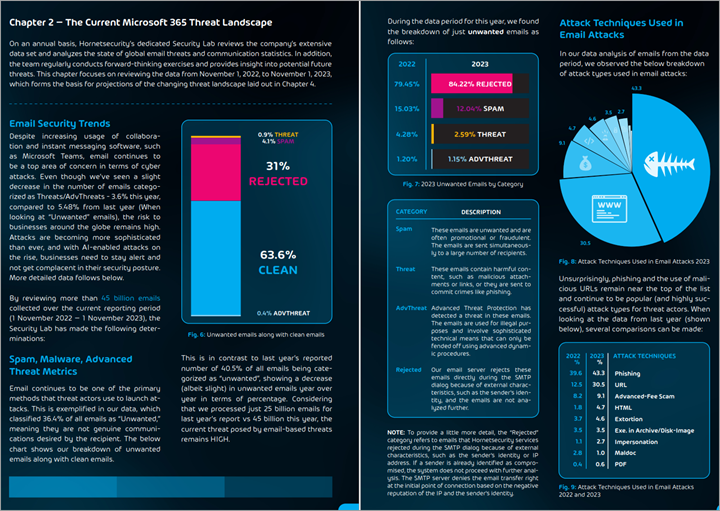
According to the report, M365 remains a popular target for cyber attackers, as it hosts a vast amount of sensitive and valuable data for businesses of all sizes and industries. The report shows that out of the 45 billion emails processed by Hornetsecurity in 2023, about 36.4% were categorized as unwanted, meaning spam, rejected, or malicious. Out of the unwanted emails, 3.6% were malicious.
The report also provides a detailed breakdown of the types and trends of malicious emails, such as:
- Phishing: Phishing remains the most prevalent type of malicious email, accounting for 43.3% of all malicious emails, which is a 4% increase from 2022. The report identifies the most common phishing techniques, such as brand impersonation, credential harvesting, and business email compromise (BEC).
- Malicious URLs: Malicious URLs are the second most common type of malicious email, accounting for 30.5% of all malicious emails, which is an 18% increase from 2022. The report reveals the most popular domains and TLDs used by attackers, as well as the most common redirection methods and landing pages.
- Malicious Attachments: Malicious attachments are the third most common type of malicious email, accounting for 26.2% of all malicious emails, which is a 22% decrease from 2022. The report shows the most prevalent file types and formats used by attackers, such as HTML, PDF, and archive files.
The report also analyzes the industry targeting, brand impersonation, and vendor overdependence of M365 attacks, and provides examples and case studies of major breaches and incidents that occurred in 2023.
The Most Critical and Emerging Cyber Security Threats
The report also identifies and discusses the most critical and emerging cyber security threats that M365 users and admins should be aware of and prepared for in 2024, such as:
- Ransomware: Ransomware is a type of malware that encrypts the victim’s data and demands a ransom for its decryption. The report predicts that ransomware will continue to be one of the most serious and widespread threats in 2024, as attackers will use more sophisticated and targeted techniques, such as double extortion, supply chain compromise, and zero-day exploits.
- Zero Trust: Zero Trust is a security model that assumes that no entity, whether internal or external, is trustworthy by default, and requires continuous verification and validation of identity and access. The report suggests that Zero Trust will become more essential and prevalent in 2024, as M365 environments will become more complex and dynamic, and as remote and hybrid work will persist.
- Artificial Intelligence: Artificial Intelligence (AI) is a branch of computer science that enables machines to perform tasks that normally require human intelligence, such as learning, reasoning, and decision making. The report warns that AI will pose both opportunities and challenges for M365 security in 2024, as attackers will use AI to enhance their attacks, such as generating convincing phishing emails, while defenders will use AI to improve their detection and response capabilities.
The Predictions and Recommendations for 2024
The report also provides predictions and recommendations for M365 users and admins for 2024, based on the analysis of the data and the trends observed in 2023, such as:
- The report predicts that M365 attacks will become more frequent, sophisticated, and targeted in 2024, as attackers will exploit the vulnerabilities and gaps in M365 security, such as misconfigurations, legacy protocols, and third-party integrations.
- The report recommends that M365 users and admins adopt a proactive and holistic approach to M365 security in 2024, by implementing best practices and standards, such as multi-factor authentication, encryption, backup, and auditing, as well as by leveraging advanced and complementary security solutions, such as Hornetsecurity’s 365 Total Protection.
- The report also advises that M365 users and admins stay informed and educated about the latest M365 security threats and developments in 2024, by following reliable and reputable sources, such as Hornetsecurity’s Security Lab, which conducts forensic analyses of the most current and critical security threats, and provides timely and actionable insights and guidance.
Example of one page from the report below…
Conclusion
Hornetsecurity’s Cyber Security Report 2024 is valuable resource for M365 users and admins who want to understand and improve their M365 security, and protect their data and business from cyber attacks. The report covers the current state of M365 security, the most critical and emerging cyber security threats, and the predictions and recommendations for 2024, based on real-world data and expert knowledge.
If you want to learn more about Hornetsecurity’s Cyber Security Report 2024, or request a free copy, visit Hornetsecurity’s website
More about HornetSecurity on ESX Virtualization Blog:
- Hornetsecurity’s 365 Threat Monitor for Microsoft 365 Review
- Hornetsecurity VM Backup V9 for VMware vSphere and Microsoft Hyper-V – Product Review
- The Importance of Security Awareness Training to successfully fight Ransomware
More posts from ESX Virtualization:
- VMware vCenter Server 8.0 U1b resolves further upgrade issues and adds bunch of security patches
- VMware vCenter Server Appliance 8.0U1a Released
- Homelab v 8.0 (NEW)
- vSphere 8.0 Page (NEW)
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)