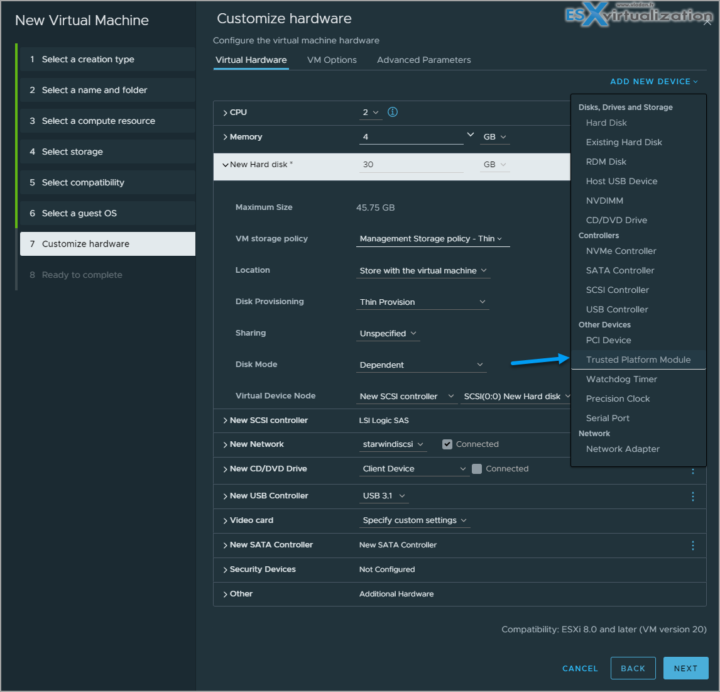
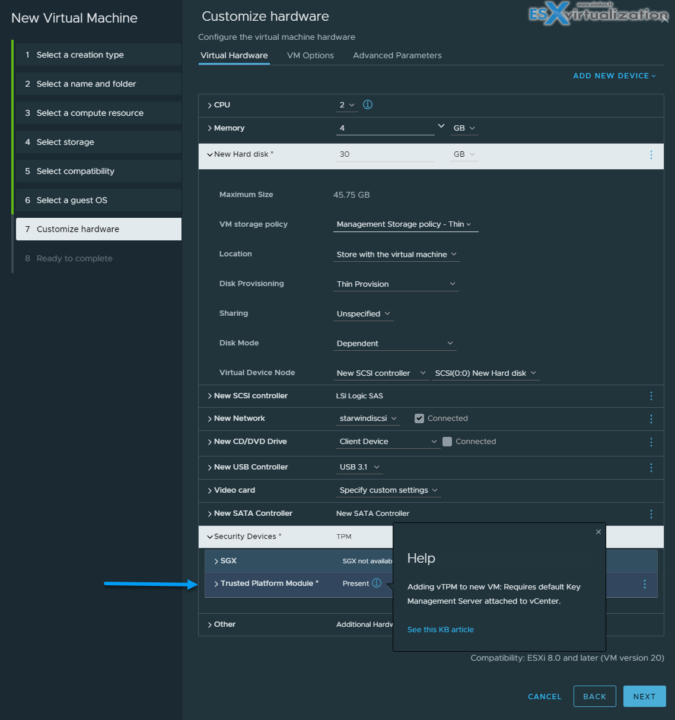
Today we have another post, VCP-DCV on vSphere 8.x Objective 1.9.1 – Recognize use cases for a virtual Trusted Platform Module (vTPM), that is part of our VCP8-DCV Study Guide Page. The guide page progress quite quickly because a lot of the content has not changed, but we're adding what's new in vSphere 8.x and also what's new compared to the previous Study Guide that is based on vSphere 7.x (Note: The exam based on vSphere 7.x will be retired the 31. Jan 2024).
vTPMs provide hardware-based, security-related functions such as random number generation, attestation, key generation, and more. When added to a virtual machine, a vTPM enables the guest operating system to create and store keys that are private. These keys are not exposed to the guest operating system itself. Therefore, the virtual machine attack surface is reduced. Usually, compromising the guest operating system compromises its secrets, but enabling a vTPM greatly reduces this risk. These keys can be used only by the guest operating system for encryption or signing. With an attached vTPM, a client can remotely attest the identity of the virtual machine, and verify the software that it is running.
There are some concerns that you should be aware of when willing to backup VMs with vTPM enabled.
Quote:
When you back up a virtual machine enabled with a vTPM, the backup must include all virtual machine data, including the *.nvram file. If your backup does not include the *.nvram file, you cannot restore a virtual machine with a vTPM. Also, because the VM home files of a vTPM-enabled virtual machine are encrypted, ensure that the encryption keys are available at the time of a restore.
Other than that, you can configure vTPM even if your ESXi does not have a physical TPM 2.0 chip installed. However, if you want to perform host attestation, an external entity, such as a TPM 2.0 physical chip, is required.
Virtualization has revolutionized the way we think about server infrastructure and the management of data centers. VMware vSphere 8 is one of the most popular virtualization platforms on the market today, and it offers a wide range of features to help businesses optimize their infrastructure. One of the most interesting features of VMware vSphere 8 is the virtual Trusted Platform Module (vTPM). In this blog post, we will explore the use cases for a vTPM within VMware vSphere 8.
Now that we understand what a vTPM is, let's explore some of the use cases for it within VMware vSphere 8:
Enhanced Security for Virtual Machines – One of the most obvious use cases for a vTPM is to enhance the security of virtual machines (VMs) running on the VMware vSphere 8 platform. By leveraging the secure storage and cryptographic capabilities of a vTPM, VMs can be better protected against attacks that attempt to compromise their data. This is particularly important for VMs that run critical workloads, such as financial or healthcare applications, that require a high level of security.
Compliance with Industry Standards – Many industries, such as finance and healthcare, have specific regulatory requirements that must be met when it comes to data security. The use of a vTPM within VMware vSphere 8 can help businesses comply with these standards by providing a secure platform for storing cryptographic keys and other sensitive data.
Encryption of Virtual Disks – Another use case for a vTPM within VMware vSphere 8 is the encryption of virtual disks. By using a vTPM to securely store the encryption keys, VMs can be protected against attacks that might try to access or modify their virtual disks. This can be particularly important for VMs that store sensitive data, such as credit card numbers or patient health records.
Protection of Cloud Infrastructure – VMware vSphere 8 is often used in cloud environments where businesses rely on the platform to provide critical services. By using a vTPM, businesses can help protect their cloud infrastructure against attacks that might try to compromise the security of the underlying platform. This can help ensure that business-critical applications and services remain available and secure.
In conclusion, the use of a virtual Trusted Platform Module (vTPM) within VMware vSphere 8 can provide businesses with a wide range of benefits, including enhanced security for virtual machines, compliance with industry standards, encryption of virtual disks, protection of intellectual property, secure multi-tenancy, and protection of cloud infrastructure. As virtualization continues to become more prevalent in modern data centers, the use of vTPMs is more and more necessary for certain workloads.
Hopefully this chapter will help you to study towards VMware VCP-DCV Certification based on vSphere 8.x. Find other chapters on the main page of the guide – VCP8-DCV Study Guide Page.
More posts from ESX Virtualization:
- Homelab v 8.0 (NEW)
- vSphere 8.0 Page (NEW)
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)