Microsoft 365 is one of the most popular and widely used cloud platforms for businesses of all sizes and industries. It offers a range of productivity and collaboration tools, such as SharePoint, Teams, and OneDrive, that enable users to work efficiently and effectively from anywhere and on any device.
However, you as a Microsoft 365 administrator, you have to ensure that your data is protected and compliant at all times. You have to monitor and control who has access to what, how they share it, and what they do with it. You have to enforce policies and rules that align with your business goals and regulatory requirements. And you have to do all this without compromising the user experience or wasting your time and resources.
It seems like it is a lot of work. Here is why you might be interested in 365 Permission Manager, a service from Hornetsecurity, you can now manage permissions and compliance for SharePoint, Teams, and OneDrive with ease and confidence. We have already blogged about this service – How 365 Permission Manager from Hornetsecurity builds a game-winning strategy for M365 Compliance.
What is 365 Permission Manager?
365 Permission Manager is a service that helps you manage permissions and compliance for SharePoint, Teams, and OneDrive. It allows you to easily monitor and audit the sharing of sites, files, and folders, and to take quick actions to prevent data breaches or violations. It simplifies the permission management process by providing a user-friendly interface and enabling bulk actions.
Some of the features and benefits of 365 Permission Manager are:
- It helps you implement the least-privilege access principle, which is a key component of the Zero Trust approach to cyber security. This means that you only grant the minimum level of access that users need to perform their tasks, and revoke it when they no longer need it.
Screenshot from Hornetsecurity website below.
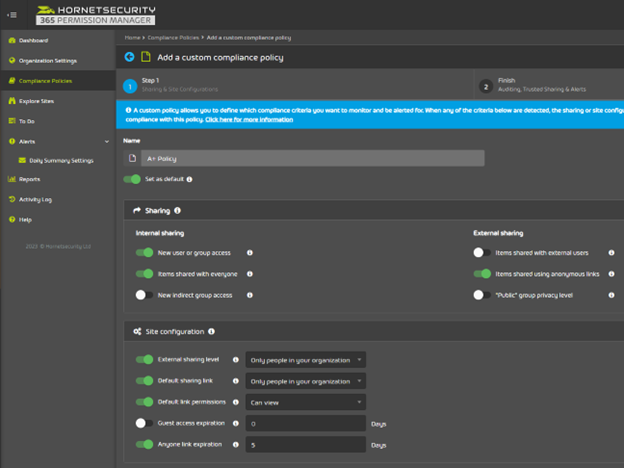
- It saves you time and effort by allowing you to perform complex tasks with a few clicks. As an example, you can grant or revoke permissions for multiple users, groups, or sites at once, or apply predefined templates for common scenarios.
- It enhances your compliance with internal and external regulations and policies, such as GDPR, HIPAA, or ISO 27001. You can easily identify and fix any issues or risks that may arise from the sharing of sensitive or confidential data, and generate reports to prove your compliance status.
- It reduces the risk of data leakage, unauthorized access, or malicious attacks by controlling and monitoring the sharing of sensitive or confidential data. You can set up alerts and notifications to inform you of any suspicious or unusual activities, and take immediate actions to stop them.
How to use 365 Permission Manager?
Using 365 Permission Manager is easy and intuitive. You can access it from any web browser, and connect it to your Microsoft 365 tenant with a few simple steps. Once connected, you can start managing permissions and compliance for SharePoint, Teams, and OneDrive.
Here are some of the things you can do with 365 Permission Manager:
- View and manage permissions for SharePoint sites, Teams, and OneDrive folders. You can see who has access to what, and what level of permissions they have. You can also add, remove, or modify permissions for individual users, groups, or sites, or copy permissions from user who has already been configured, to one or more users with same requirements.
- Monitor and audit the sharing of sites, files, and folders. You can see who shared what, with whom, and when. You can also see the status of the sharing links, such as whether they are active, expired, or revoked. You can also filter and sort the data by various criteria, such as site, user, date, or type of sharing.
- Enforce policies and rules for sharing and compliance. You can set up policies and rules that define the conditions and actions for sharing and compliance. For example, you can require approval for external sharing. You can also set up alerts and notifications to inform you of any policy violations or risks, and take immediate actions to resolve them.
- Generate reports and dashboards for permissions and compliance. You can create and export reports and dashboards that show the status and trends of permissions and compliance. These reports and dashboards are used to demonstrate your compliance status and performance, and to identify areas for improvement.
Why choose 365 Permission Manager?
365 Permission Manager is the ultimate solution for managing permissions and compliance for SharePoint, Teams, and OneDrive. It offers you the following advantages:
- It is a cloud-based service that does not require any installation or maintenance. You can access it from any web browser, and connect it to your Microsoft 365 tenant with a few simple steps.
- It is a user-friendly and intuitive service that does not require any technical skills or training. You can easily navigate and use the interface, and perform tasks with a few clicks.
- It is a comprehensive and flexible service that covers all aspects of permissions and compliance. You can manage permissions and compliance for SharePoint, Teams, and OneDrive, and customize the service to suit your needs and preferences.
- You can generate reports to comprehend internal and external permissions like external guest access or anonymous links.
How to get started with 365 Permission Manager?
If you are interested in trying out 365 Permission Manager, you can request a Free trial from Hornetsecurity. You can also contact them for more information or a demo.
Final Words
Security of data, together with compliance, becomes more and more important. Only a couple of years ago IT admins were more occupied to get better performance of their IT infrastructure and the security slipped somehow at the second place. Things are changing quickly with high performant servers, hosts with latest NVMe devices and in-memory data caching optimizations in today’s landscape. As ransomware threats evolve, staying compliant with security standards is not just a regulatory requirement but a critical component of an organization’s cyber defense strategy.
More posts from ESX Virtualization:
- Nutanix Community Edition
- Another VMware Alternative – Verge.IO
- How to install and run Xen Orchestra Lite
- XCP-NG Virtualization Platform with management by Xen Orchestra
- Best VMware Alternatives – ESXi FREE is DEAD
- vSphere 8 U2 Identity Federation with Entra ID/Azure AD – vSphere never sees the users credentials
- VMware vCenter Server Converter 6.4 Released
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)
