Ransomware-proof backup architectures are becoming the new standard. Your backup architecture and your backups are the hacker's N°1 target because without your backups you're most likely open to negotiate and pay the ransom. That's the reality. I know it's not that simple, but how about making the life more difficult for those hackers? How about putting in place a Virtual Tape Library (VTL) which is isolated from your main backup server? Let's have a look at both scenarios (same server or separate host).
If you remember my last article on StarWind VTL: Fortifying Your Backup Infrastructure Against Ransomware? We talked about how this virtual tape library is a game-changer for keeping ransomware away, turning your backups into an impenetrable fortress with air-gapping and immutable storage. Well, today I'm following up with some best practices from StarWind, to make sure you're not leaving your infrastructure exposed. Because let's face it – too many admins take backups for granted, unprotected.
Ransomware isn't slowing down, it's evolving, so neglecting your backups is like leaving your front door wide open in a bad neighborhood. In this post, I'll draw from StarWind's official best practices guide to give you actionable advice tailored for those who've been slacking on security.
We'll cover installation, configuration, maintenance, and most importantly – ransomware-proofing steps. My goal? Inspire you to audit your setup today and implement these tips before it's too late. Let's dive in and fortify those backups!
Why Admins Overlook Backup’s security (And Why It's a Ticking Time Bomb)
I've seen it time and again in forums and chats with fellow admins: backups get deprioritized because they're “boring” or “just work.” You're busy fighting daily fires—patching servers, scaling VMs, dealing with user complaints— so the backup infrastructure sits in the corner, unmonitored and under protected.
However, according to recent reports, over 70% of ransomware attacks now target backups directly. Hackers know that if they encrypt your primary data and your recovery points, you're done. Paying the ransom becomes the only option, and that's a terrible scenario, indeed.
If your backups aren't air-gapped, immutable, or isolated, they're in trouble. Tools like StarWind VTL change that by emulating physical tapes on modern disk and cloud storage, making them invisible to malware. But even with VTL, sloppy implementation can undo all that goodness. The best practices I'm sharing today are pulled straight from StarWind's playbook, emphasizing security isolation and performance tweaks. Think of this as your checklist to avoid becoming a cautionary tale.
Installation Best Practices: Build a Solid Foundation
Installing StarWind VTL is straightforward, but rushing it can leave gaps hackers can exploit. If you’ve been underestimating your setup process, treat installation like building a vault—secure and deliberate.
You’ve got two main options: all-in-one or separated. For greenfield setups (starting fresh), go all-in-one. Install your backup software (like Veeam or NAKIVO) and StarWind VTL on the same physical server with a dedicated Storage Repository. This keeps things simple and minimizes network bottlenecks, perfect for smaller environments.
In brownfield setups with legacy systems, separation is smarter. Run your backup software in a VM (inside or outside your cluster) and keep VTL on a dedicated physical server. This gives you tighter control over permissions and limits damage if something goes wrong. In case your virtual infra gets corrupted, fine. Just rebuild a backup server > re-connect to the VTL > restore and you're back in business.
Pro tip: Use a separate user account for backup server (with 2FA) access and a dedicated service user for the backup app. Without 2FA, your credentials might leak, hackers can’t easily jump to your VTL.
Storage matters – don’t cut corners. Use spindle disks for high-capacity, cost-effective backups (RAID 5, 50, 6, or 60 for redundancy and affordability) – if that's still the case because SSD's are fast becoming cheap!
If fast recovery is critical, go for all-flash or hybrid arrays to shrink restore times from days to hours. Here’s a wake-up call for admins who’ve overlooked this: If your storage is shared with production workloads, stop now. Dedicate it solely to VTL to isolate it from your main environment. Shared storage is a hacker’s playground—malware spreads fast.
During installation, enable the firewall from the get-go and keep your OS and antivirus updated. I’ve heard stories of admins skipping patches, only to get burned by exploits. Grab the free version of StarWind VTL to test it out—no risk, all reward.
Note: There is also version for Linux, you'll see it in the links section after the post.
Configuration Tips: Locking Down against Ransomware
Configuration is where you make your backups bulletproof. Many admins breeze through this, but with VTL, intentional steps are key to ransomware resilience.Start with networking. Ensure enough bandwidth to avoid bottlenecks—1GbE handles up to 100 MB/s backups, but scale to 10GbE for bigger jobs. Dedicate interfaces and put them on a separate VLAN to isolate traffic. If you’ve underestimated network segregation, you’re at risk—malware loves unsegmented networks.
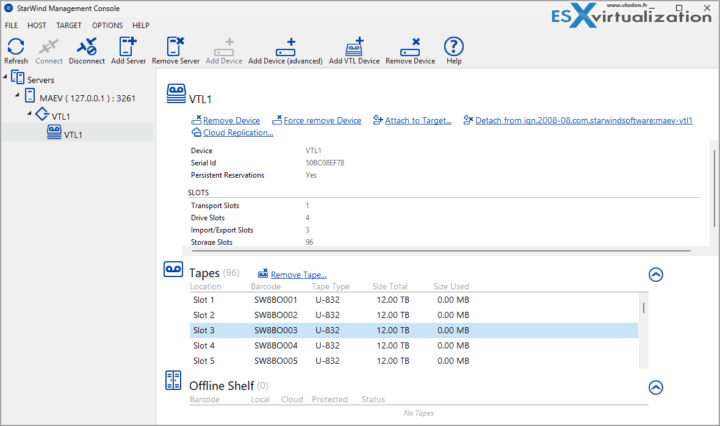
The real power of VTL lies in air-gapping and immutability. It stores data as virtual tapes, using protocols that file-based malware can’t touch. Enable Write-Once-Read-Many (WORM) mode for true immutability—no deletions or changes allowed.
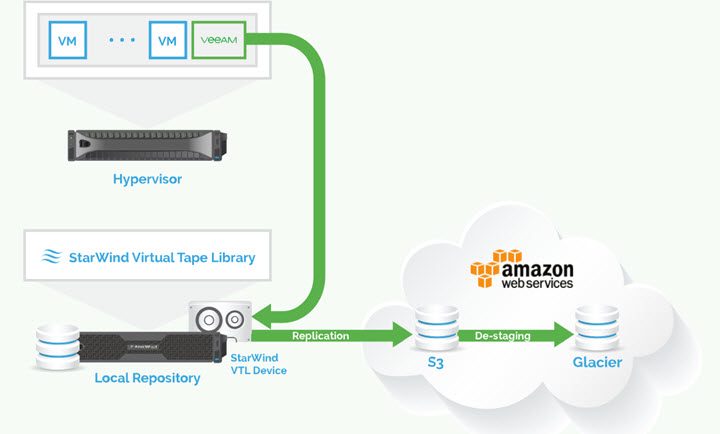
Pair this with cloud tiering to nail the 3-2-1 rule: three copies, two media types, one offsite. Offload tapes to object storage like AWS S3, Azure Blob, or on-prem Cloudian. Again, StarWind has special how-to step-by-step guides in our links section!
It’s a low-maintenance way to archive cold data to budget-friendly tiers like Azure Archive (as cheap as $1 per month per TB). If you’ve been skipping offsite copies, this is your safety net—ransomware can’t reach cloud-isolated backups.For iSCSI connections, enable CHAP authentication and strict access controls.
Disable file shares on the VTL host—they’re an unnecessary risk. Critically, do not join the VTL server to your domain. Domain-joined servers are easy targets for lateral attacks. Keep it standalone with local accounts. If you’ve been running VTL domain-joined for convenience, audit that now—it’s a common oversight that exposes everything.VTL integrates seamlessly with backup software like Veeam. Test restores regularly; nothing exposes an overlooked setup like a failed recovery drill.
Maintenance and Security: Stay Proactive, Stay Safe
Installation and config are just the beginning—maintenance keeps your backups resilient. Admins who deprioritize this risk outdated systems that ransomware can exploit.
Keep everything patched: OS, antivirus, and VTL software. StarWind releases regular updates, so enable auto-checks in the Management Console. Check their resource library for detailed guides or hit their forums for community tips. If you’re stuck, their support form is quick to respond.
Security maintenance is non-negotiable. Isolate VTL storage from production with dedicated disks or arrays. This “quarantine” ensures backups stay clean even if your main environment is compromised. Review access logs and rotate credentials often. For offsite redundancy, automate cloud replications to maintain at least one immutable offsite copy—your ace in the hole for ransom-free recovery.
If you’ve underestimated antivirus, rethink that. Run it on the VTL host, but whitelist VTL processes to avoid false positives. Use StarWind’s built-in alerts to catch suspicious activity early.
For performance, fine-tune retention policies to balance storage and compliance. Virtual tapes can be ejected and archived efficiently, saving space without sacrificing security.
Real-World Advice: Don’t Let Oversight Bite You
I’ve been in the virtualization trenches long enough to know that overlooking backups feels fine—until it isn’t. One admin I know skipped isolation and lost weeks of data to a sneaky ransomware strain. Don’t let that be you. Start small: Download StarWind VTL, apply these best practices, and run a full backup test. The cost savings from ditching physical tapes for disk/cloud are huge, but the real win is knowing your data is safe.
Links:
The setup guide for StarWind VTL deployed as a Windows application is available here:
https://www.starwindsoftware.com/resource-library/starwind-virtual-tape-library-deploy-using-local-storage/
The guide for deploying StarWind VTL Linux ISO image is here:
https://www.starwindsoftware.com/resource-library/starwind-virtual-tape-library-configuration-guide-for-local-storage-vtl-deployed-as-a-linux-iso-using-gui/
Additionally, StarWind VTL on Windows supports the replication of virtual tapes to cloud object storage. You can find the setup guide for configuring StarWind VTL cloud replication to Amazon S3, Backblaze B2, Microsoft Azure, and Wasabi here:
https://www.starwindsoftware.com/resource-library/starwind-virtual-tape-library-deploy-using-cloud-storage/
The setup guide for configuring replication to Cloudian and S3-compatible cloud object storage is available here:
https://www.starwindsoftware.com/resource-library/starwind-virtual-tape-library-deploy-using-object-storage/
For more details, dive into StarWind’s best practices guide.
StarWind VTL Product page here.
Final Words
Ransomware doesn’t care if you’re too busy to secure your backups. By following these StarWind VTL best practices—solid installation, tight configuration, proactive maintenance—you’re not just protecting data; you’re safeguarding your organization’s future. It’s about resilience, not perfection. Stay sharp, keep those backups locked down, and until next time, happy administrating!
More posts about StarWind on ESX Virtualization:
- FREE version of StarWind VSAN vs Trial of Full version
- Installation of StarWind VSAN Plugin for vSphere
- StarWind VSAN with new UI and deployment options
- Backup Appliance with NVMe Speed and GRAID – StarWind Backup Appliance
- Exploring StarWind VSAN: High Availability, Cost Savings, and Performance
- StarWind V2V Converter The Cutting-Edge Upgrade: StarWind V2V Converter’s April 2024 Innovations
- What is StarWind Tape Redirector (FREE) and what’s the benefits?
- 5 Easy Steps to be more resilient with Two Hosts only – StarWind VSAN
- How StarWind VSAN solution can save you money and energy in ROBO environments
- 2-Nodes clusters without Witness – StarWind VSAN Heartbeat Failover Strategy
- You can’t extend backup window – Check NVMe Backup Appliance from StarWind
- Replacing Aging Hardware SAN Device by a Software – StarWind VSAN
- StarWind V2V Converter (PV2 Migrator) FREE utility
- Cluster with 2-Nodes only – How about quorum?
- StarWind VSAN Latest update allows faster synchronization with storing synchronization journals on separate storage
- How to Update StarWind VSAN for VMware on Linux- Follow UP
- StarWind SAN & NAS software details for VMware and Hyper-V
- Free StarWind iSCSI accelerator download
- VMware vSphere and HyperConverged 2-Node Scenario from StarWind – Step By Step(Opens in a new browser tab)
- How To Create NVMe-Of Target With StarWind VSAN
- Veeam 3-2-1 Backup Rule Now With Starwind VTL
- StarWind and Highly Available NFS
- StarWind VSAN on 3 ESXi Nodes detailed setup
- VMware VSAN Ready Nodes in StarWind HyperConverged Appliance
More posts from ESX Virtualization:
- 5 New VMware Certifications for VVF and VCF
- VMware Alternative – OpenNebula: Powering Edge Clouds and GPU-Based AI Workloads with Firecracker and KVM
- Proxmox 9 (BETA 1) is out – What’s new?
- Another VMware Alternative Called Harvester – How does it compare to VMware?
- VMware vSphere 9 Standard and Enterprise Plus – Not Anymore?
- VMware vSphere Foundation (VVF 9) and VMware Cloud Foundation (VCF 9) Has been Released
- Vulnerability in your VMs – VMware Tools Update
- VMware ESXi FREE is FREE again!
- No more FREE licenses of VMware vSphere for vExperts – What’s your options?
- VMware Workstation 17.6.2 Pro does not require any license anymore (FREE)
- Migration from VMware to another virtualization platform with Veeam Backup and Replication
- Patching ESXi Without Reboot – ESXi Live Patch – Yes, since ESXi 8.0 U3
- Update ESXi Host to the latest ESXi 8.0U3b without vCenter
- Upgrade your VMware VCSA to the latest VCSA 8 U3b – latest security patches and bug fixes
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- vSphere 8.0 Page
- ESXi 7.x to 8.x upgrade scenarios
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster

Leave a Reply